Whether you’re a multi-billion dollar company or an individual using email for personal purposes, you’re not safe from one of the most common scams online – email spoofing.
That sounds scary, right? If we’re all prone to something malicious like email spoofing, we need to learn a little about it to take the right precautions to avoid falling into its traps.
What is Email Spoofing?(Definition)
Email spoofing is a cyber attack in which a scammer or hacker sends emails with a forged or fake sender address. The aim is to trick the recipients into thinking that the emails are from a trusted source and get them to open or respond to the message.
Spoofed emails are dangerous and can pose a massive threat to your privacy and security. Typically, these emails are sent so the hackers can send malware, take over your online accounts, or steal funds or money.
But the question is – how exactly does email spoofing work? Let’s find out!
How Does Email Spoofing Work?
Email spoofing can be done easily with the help of a working SMTP (Simple Mail Transfer Protocol) server and popular email platforms like Gmail or Outlook.
Since emails have three main elements – an envelope, a message header, and a message body, a hacker can compose an email and then forge the fields within that email and put whatever they want into it. They can customize the information in the areas such as FROM, REPLY-TO, SUBJECT, etc.
And because SMTP does not provide a way to authenticate addresses, the email program reads what’s in the fields and generates what the recipient sees. So when the recipient gets the email, it appears to come from a forged address.
For example, an attacker or hacker might create an email that looks like it is sent from PayPal. It might contain a message asking recipients to click a link to authenticate or change their account password. This might trick the recipient into giving their credentials and account details, resulting in their money being stolen.
Reasons for Email Spoofing
The reasons for email spoofing are straightforward and mainly intended for criminal purposes. Some of the most common reasons behind this malicious act include the following:
1. Identity Theft or Hiding Identity
One of the main reasons behind email spoofing is to hide or conceal identity. It allows the attackers or hackers to remain anonymous or pretend to be someone else to earn their targets’ trust and then gather confidential information from them.
2. Avoiding a Spam Blacklist
A majority of email providers let its user create a blacklist that helps them filter out spam. Hence hackers spoof their email addresses to slip past the filters undetected and avoid being included in the spam blacklist.
3. Tarnishing the Reputation of the Sender
Usually, a spoofed email contains false information and malicious links that are intended to harm the recipient in some way or the other. Attackers sometimes use this method to send malware via emails to tarnish the image or reputation of organizations or persons.
4. Intending to do Personal Damage
Email spoofing can be used to gain the target’s personal information, business contacts, social media accounts, and more. Access to this can allow the attacker to interrupt the target’s digital life and cause harm or damage to their personal life.
The dangers of email spoofing are beyond your control once you fall into its trap, and it is often quite easy to be trapped by it. It exploits the human factor that no one double-checks the emails they receive.
This brings us to the next question – how exactly do hackers spoof your email address? Let’s find out in the next section!
How Do Hackers Spoof Email Addresses?
Email spoofing is mainly done by forging the email syntax, but it varies depending on which part of the email the hacker tries to forge. Here are 3 different ways that attackers spoof emails:
1. Email Spoofing via Display Name
Spoofing via display name is a type of email spoofing in which the display name of the email sender is forged. This can be easily done by simply registering a new email account with the same name as the person being impersonated.
So if you ever receive an email from a celebrity asking for money or access to your bank details, then you can be sure it is spoofing via display name. This type of email spoofing often gets past the security measures as it won’t get filtered as spam and is quite effective as email apps don’t show metadata on smartphones.
2. Email Spoofing via Legitimate Domains
In the case of email spoofing via legitimate domains, the attacker may use a trusted email address in the FROM header. This means the display name and the email address will show the wrong information.
For this type of spoofing, the attacker doesn’t need to hack into the target’s internal network; they only need to use SMTP servers that allow connections without authentication which lets them manually specify the “To” and “From” addresses. This is very dangerous as many company email domains don’t use any countermeasures for verification.
3. Email Spoofing via Lookalike Domains
Spoofing via lookalike domains is an email spoofing in which the hacker registers and uses a domain similar to the impersonated domain. The change is often minimal, and a receiver might not notice the difference.
For example, something like @gma1l.com instead of @gmail.com. Hackers usually do this when a domain is protected, and spoofing isn’t possible. With this method, the emails bypass spam checks due to being legitimate mailboxes.
Now that you know how hackers can spoof email addresses, you need to learn to protect yourself from them. Let’s find out how in the next section!
How to Protect from Email Spoofing?
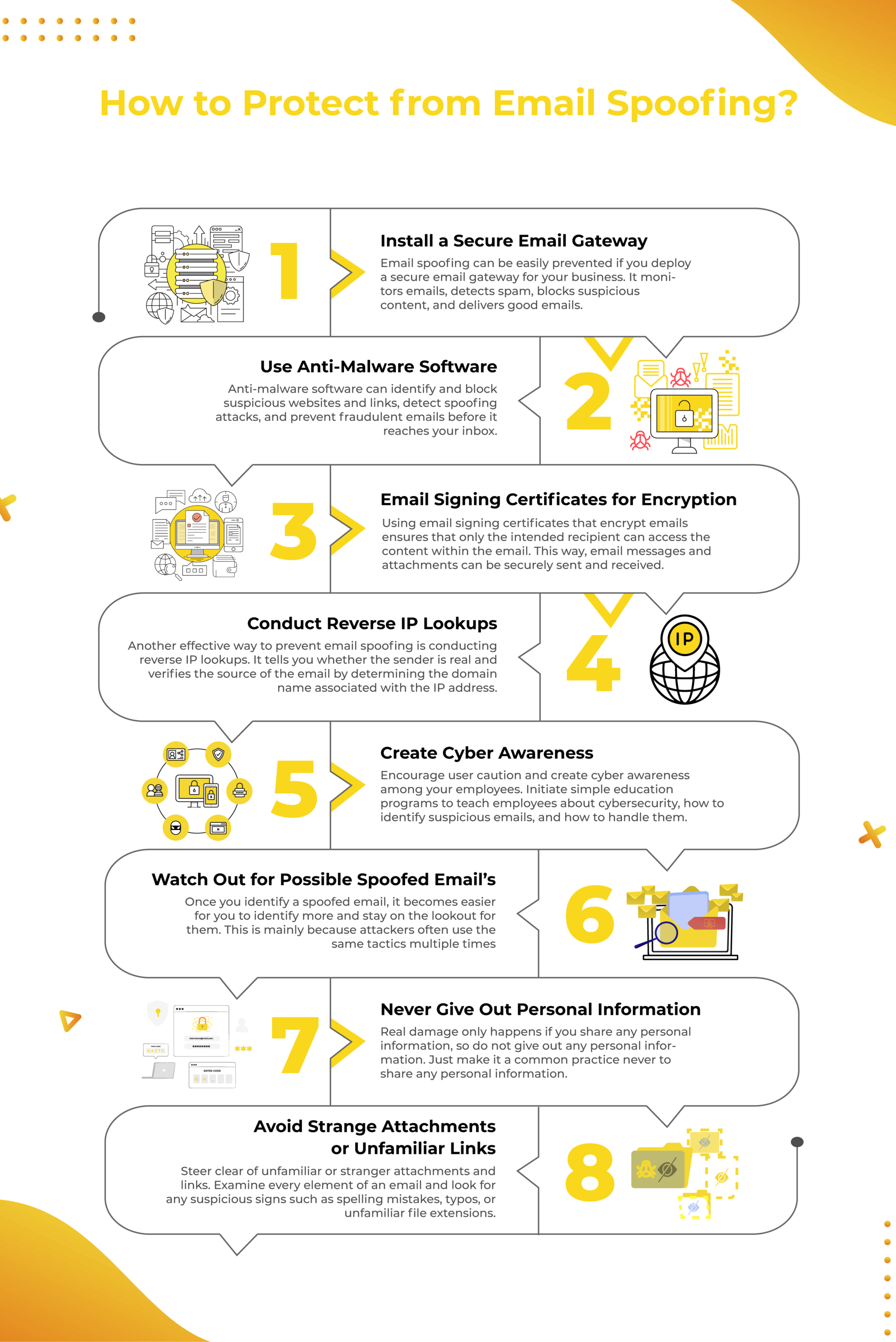
1. Install a Secure Email Gateway
Email spoofing can be easily prevented if you deploy a secure email gateway for your business. A Secure Email Gateway (SEG) is software that monitors emails sent and received. It detects most malware, spam, and phishing attacks.
An email gateway ensures that your email is secure by blocking inbound and outbound emails with suspicious elements or not meeting the security policies that a business puts in place. The email gateway protection prevents unwanted emails and only delivers the good ones.
2. Use Anti-Malware Software

Another software that can help you with preventing email spoofing is anti-malware software. These software programs can identify and block suspicious websites and links, detect spoofing attacks, and prevent fraudulent emails before it reaches your inbox. Anti-malware software can also work like a force field that protects your system from spoofed emails.
3. Use Email Signing Certificates for Encryption
One popular way to prevent email spoofing is by using email signing certificates that encrypt emails. Only the intended recipient can access the content within the email.
Email encryption certificates use asymmetric encryption, where a public key encrypts the email and sends it to the recipient. The recipient then gets a private key to help them decrypt the message. This way, email messages and attachments can be securely sent and received.
Moreover, to ensure your recipients that the source of the email and its contents are valid and authentic, you can also add your digital signature to it.
4. Conduct Reverse IP Lookups
A simple yet effective way to identify email spoofing is by conducting reverse IP lookups. It tells you whether the sender is real, verifies the email’s source by determining the domain name associated with the IP address, and even tells you where the email came from.
You can use online reverse lookup tools to determine the domain name associated with the IP address. In this case, if the IP address differs from where the email was supposed to come from, you can easily identify the email spoofing attack. This makes it an email spoofing test.
You can also publish a Domain Name System (DNS) record that states who can send emails on behalf of your domain so that the messages can be inspected before downloading. This will help you block or reject content before it causes any harm.
5. Create Cyber Awareness
You can rely on technology and new software to combat email spoofing. Still, it becomes much more effective if you encourage user caution and create cyber awareness among your employees.
If your employees are unaware, a fake email might look real. So, you need to initiate simple education programs to teach employees about cybersecurity, how to identify suspicious emails, and how to handle them.
While training your employees about cyber awareness, you must periodically update the training materials and teaching methods to keep up with the new developments in the email spoofing area.
6. Watch Out for Possible Spoofed Email Addresses
More often than not, the kind of email addresses that you see in messages are familiar or predictable, so you can learn to watch out for unknown or suspicious email addresses. If you get a strange email, you can verify its origin before interacting with the content.
Once you identify a spoofed email, it becomes easier for you to identify more and stay on the lookout for them. This is mainly because attackers often use the same tactics multiple times. So always stay vigilant!
7. Never Give Out Personal Information
This one is a no-brainer – never give out personal or confidential information. In most cases, even if a spoofed email makes it into your inbox, real damage only happens if you share any personal information. So the simplest thing you can do is not give out personal information. Make it a common practice never to share personal information, and voila, you will be significantly limiting the damage of an email spoofing attack.
8. Avoid Strange Attachments or Unfamiliar Links
Here’s another no-brainer – steer clear of unfamiliar or stranger attachments and links. You can do this by examining every element of an email and looking for any suspicious signs, such as spelling mistakes, typos, or unfamiliar file extensions. You can also try to find out the source of a link by right-clicking or long tapping it.
Wrap Up
There’s no denying that email spoofing attacks will happen at some point. So it’s up to us to take the right measures to prevent or identify it before it causes any real damage.
By following these simple methods, you can ensure that your inbox is safe from the malicious intentions of attackers. We hope that we have helped you learn a little about email spoofing and how to tackle it. Stay safe, folks! Happy emailing!
Further Reads
VPN: How Does it Work & How to Choose the Right One?
9 Best Email Cleaners in 2023 (Paid & Free)
9 Best Spying Tools to Keep Eye on Competitors!
11 Email Verification Tools to Check Out in 2023
21 Gmail Plugins for Smart Professionals!
The 11 Best Email Tracking Tools & Software!